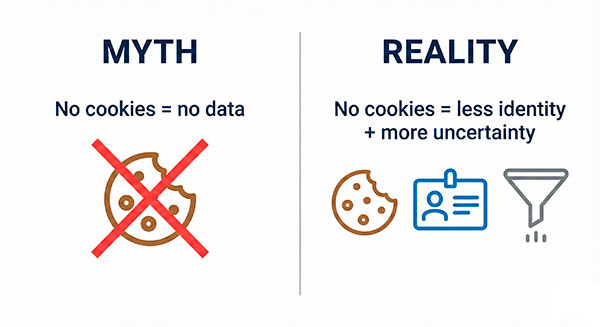
The biggest myth is that “cookieless” means “you can’t measure anything.”
In reality, you can still measure a lot—especially within a single visit. What you lose is the easy ability to recognize the same person across time, devices, and domains. That makes some reports less reliable, and it forces you to be honest about uncertainty.
Here’s the practical definition we’ll use:
Cookieless = less identity, more context.
You’ll lean on session context, page context, and well-designed events—rather than long-lived user IDs stored in the browser.
What “cookieless” really means
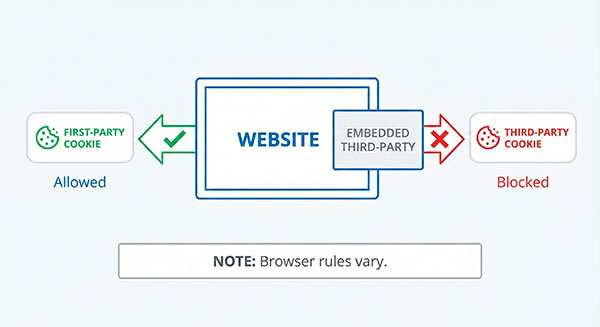
No third-party cookies (but first-party still exist)
This is the most common scenario. Third-party cookies are the ones set by another domain (often via embeds). Many browsers restrict these in different ways, and those rules keep evolving.
- What still works: most on-site funnels, basic referrer/UTM capture (when available), and session analytics.
- What breaks first: cross-site ad measurement and anything that depends on third-party identifiers.
If you want a browser-level feel for these restrictions, skim Tracking Prevention in WebKit and Enhanced Tracking Protection in Firefox.
No persistent identifiers (sessions only)
Here you treat each visit as its own island. You might still use an in-memory session ID during the visit, but you don’t try to recognize the browser tomorrow.
- Strong: session funnels and on-site UX improvements.
- Weak: returning user metrics, cohorts, frequency caps, and long lookback attribution.
This is the world where event tracking without cookies becomes a design problem: you must make each event informative enough to stand on its own.
No storage at all (strict mode / high privacy)
This is the toughest mode. No cookies, no localStorage, no persistent IDs—sometimes not even session storage.
- Still possible: counting server-side hits, measuring page-level behavior, and capturing coarse context that arrives with the request.
- Not possible (reliably): deduplicating users, recognizing returning sessions, and building stable user journeys.
If you need a quick refresher on what cookies are and why they matter for “state,” MDN’s HTTP cookies guide is clear and non-salesy.
What you can still measure pretty well (even with strict privacy)
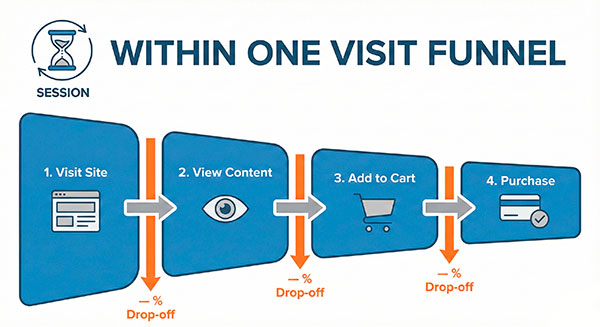
On-site behavior funnels (within a session)
Session funnels are the “happy place” for cookieless setups.
Example (e-commerce, same visit):
product_view→add_to_cart→begin_checkout→purchase
Even if you can’t recognize the same person tomorrow, you can still answer:
- Which checkout step drops the most?
- Which product pages lead to add-to-cart more often?
Content engagement that doesn’t need identity
Engagement events can work well because you’re not trying to identify a person—just measure what happened.
Example (content):
article_viewscroll_50copy_textoutbound_click
The key is to avoid vanity events. Track actions that mean something, not every hover.
Technical signals that remain (but are limited)
Most requests still carry basic context:
- landing page and path
- referrer (sometimes absent or trimmed)
- device category (coarse)
- language
- timestamp
- approximate geography (often coarse, and sometimes masked)
Use these signals to improve UX and content decisions—not to build “secret identity graphs.”
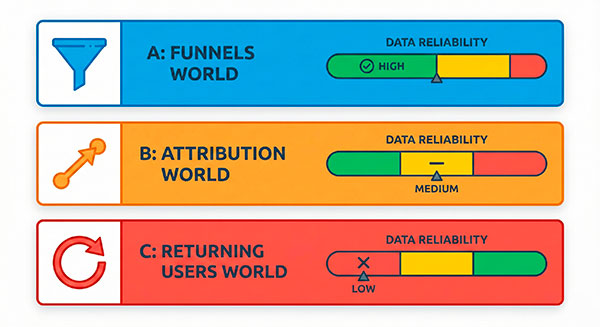
What becomes weak (and why dashboards start “lying”)
Returning users, cross-device journeys, and deduplication
Once you can’t rely on persistent identifiers, “users” becomes a fuzzy concept.
- One person can look like 3 different users (phone + laptop + tablet).
- Or 3 people can look like 1 (shared office machine, family iPad).
So reports like “returning users,” “days to convert,” and “user lifetime value” can degrade fast.
Marketing attribution gets noisier first
Attribution is where most teams feel pain early, because marketing workflows expect clean identity.
In attribution in a cookieless world, you should assume:
- more “direct / none”
- shorter observable journeys
- fewer confidently linked touchpoints
That doesn’t mean “marketing is unmeasurable.” It means you need to treat attribution as directional, and lean more on experiments, incrementality thinking, and on-site funnel health.
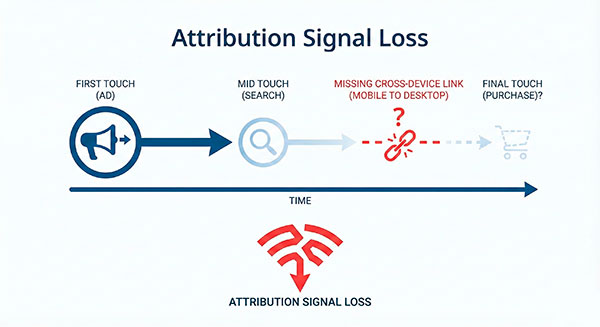
Conversions can be estimated, not observed
When identity is incomplete, some systems fill gaps with statistics. That can be useful—but it’s not the same as measurement.
- Observed: “We saw this exact visit convert.”
- Estimated: “Based on patterns, we think X conversions happened.”
Those estimates are often called modeled conversions. They can help with trend direction, but you should label them clearly and avoid pretending they’re exact.
The privacy-first building blocks (what you’re actually allowed to do)
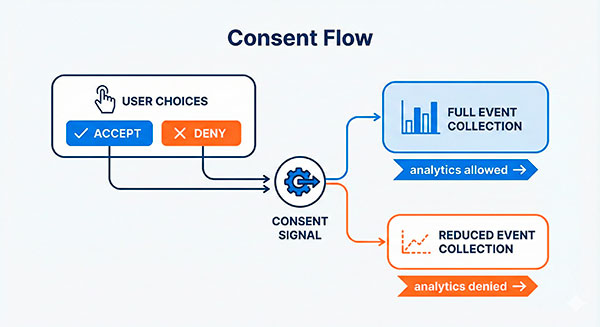
Consent layer: what must be gated, what can be “essential”
If you operate in regions with strict privacy expectations, you need a clear consent story.
Usually this means:
- You classify tracking into categories (functional, analytics, marketing).
- You collect consent choices.
- Your tracking behavior changes based on those choices.
That’s typically managed via a consent management platform (CMP).
If you need a baseline on what “valid consent” means in practice, bookmark the EDPB’s guidance: Guidelines 05/2020 on consent. For a practical cookies-focused view, the UK regulator also has a clear overview: Cookies and similar technologies (ICO).
One common approach is to send consent signals downstream so your collection logic can react. Some teams call that consent mode—but the important part is the behavior, not the label: “no consent” should mean reduced collection and no hidden workarounds.
Client-side vs server-side collection
Client-side tracking is easy to deploy—but it’s also where many restrictions bite: browser storage limits, tracking prevention, extensions, network conditions.
Server-side collection can improve stability because you control the endpoint and reduce some client breakage. It also helps you centralize filtering, validation, and security.
This is where first-party data collection becomes a practical architecture choice: you’re collecting events directly to your own domain/endpoint, then processing them responsibly.
The minimum viable identity (when you truly need it)
If your product has logins, you already have a clean identity moment: authentication.
- If someone logs in, you can link events to an account because the user chose to identify themselves.
- If they don’t log in, don’t try to “guess” identity with sneaky techniques.
A simple rule:
- Use account ID only after login.
- Otherwise, stay session-based.
And yes: do not rely on fingerprinting. It’s brittle, increasingly blocked, and it puts you on the wrong side of user trust.
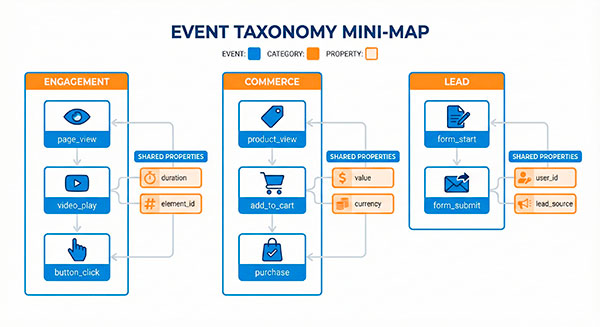
Event design for cookieless setups (your data lives or dies here)
A small, strict event schema that stays useful
Cookieless setups punish noisy tracking. You want fewer events, with better meaning.
Good cookieless event design looks like:
- clear event names (verbs)
- consistent property keys
- stable definitions that don’t change every sprint
This is the core of event schema design: you’re building a “behavior language” your team can trust.
Minimize data on purpose
If you only remember one privacy principle, make it this: collect less.
That’s not just legal caution—it’s engineering sanity. Less data means fewer mistakes, fewer leaks, and fewer debates later. This is the spirit of data minimization.
Practical do’s and don’ts:
- Don’t send emails, phone numbers, or full names in event properties.
- Avoid free-text fields that users can type into (they often contain personal info).
- Prefer categorical values over raw strings.
Recommended core properties (practical list)
A strong minimum set (adapt to your product):
event_name(e.g.,add_to_cart)event_timepage_urlreferrer(when available)content_idorproduct_idui_location(e.g., “header”, “pricing_table”)value+currency(for revenue-ish events)consent_state(simple boolean or category set)session_id(only session-scoped in stricter worlds)
Implementation patterns (simple, realistic, and not tool-specific)
Pattern 1: “Session-strong” tracking (works almost everywhere)
This is the default for most websites:
- measure funnels and engagement inside a visit
- optimize UX based on drop-offs
- keep reporting honest about user identity
Pattern 2: Server-side collection endpoint (for stability)
If you want more control, you can send events to your own endpoint first, then route them to storage/reporting.
This is often described as server-side event tracking.
It helps with:
- validation (reject broken events)
- consistent enrichment (add server timestamp, normalize URLs)
- reducing client fragility
For browser-side testing/debugging around third-party cookie changes, Chromium maintains practical notes here: Third-Party Cookie Deprecation Testing and Debugging.
Pattern 3: Logged-in tracking (best accuracy, smallest scope)
If your product has accounts, use that moment carefully:
- link events to account ID after login
- keep pre-login behavior session-based
- keep access controls tight
This gives you the most reliable cohorts without doing anything shady.
QA checklist: prove your events work under real conditions
Test matrix
Your events should work across:
- consent accepted vs denied
- Safari / Firefox / Chromium-based browsers
- adblocker on vs off
- logged in vs logged out
- cross-domain flows (if you have them)
Validation rules
At minimum, validate:
- required properties exist
- IDs match expected formats
- currency/value are sane
- event names come from an allowlist
- duplicates are handled (same event fired twice)
Cookieless-ready checklist
- Events still fire when analytics consent is denied (but with reduced payload)
- Funnels are consistent within a single session
- No personal data is sent in properties
- Key events have stable definitions (no “it depends on the sprint”)
- You can debug events in at least two browsers with tracking protection enabled
- Reports clearly label anything user-based as “directional”
Reporting that doesn’t oversell precision
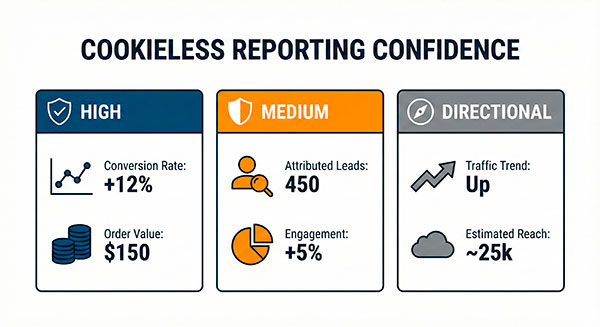
Dashboards to trust
These tend to remain solid:
- session funnel conversion rates
- step drop-off by page/template
- feature adoption within a visit
- error and performance correlations (if you capture them)
Dashboards to label as “directional”
These can still be useful, but require caution:
- returning users
- user cohorts over weeks/months
- multi-touch attribution
- cross-device journeys
Communicating uncertainty
A simple way to communicate cookieless reality:
- “This funnel is high confidence (session-scoped).”
- “This cohort is medium confidence (partial identity).”
- “This attribution view is directional (missing touchpoints).”
Tracking plan template (copy-paste format)
Below is a lightweight tracking plan template you can paste into a doc or spreadsheet:
| Business question | Event | Trigger | Required properties | Consent category | Source | Owner | QA notes |
|---|---|---|---|---|---|---|---|
| Where do users drop in checkout? | checkout_step_view | Step page loads | step_number, page_url, session_id | Analytics | Client | PM | Test deny/accept consent |
| What content drives outbound clicks? | outbound_click | Click external link | target_domain, ui_location, page_url | Analytics | Client | Analyst | Validate domain parsing |
| Do users use search before purchase? | site_search | Search submit | query_length, results_count | Analytics | Client | Dev | Don’t send raw query |
Mini-table: which questions are cookieless-friendly?
| Question | Cookieless-friendly? | Notes |
|---|---|---|
| Which checkout step drops most? | Yes | Session funnel is strong. |
| Which CTA placement gets clicks? | Yes | Works with ui_location. |
| How many returning users do we have? | Sometimes | Depends on identity rules and browser limits. |
| Which channel “caused” the purchase? | Weak | Touchpoints can be missing or unlinked. |
| What’s the 30-day user LTV? | Weak | Requires stable user identity over time. |
| What pages create confusion? | Yes | Use scroll, rage-click proxies, error events. |
Summary: realistic expectations (the 10-bullet cheat sheet)
- Cookieless doesn’t kill measurement—it kills easy identity.
- Session funnels are your most reliable foundation.
- Expect “users” to be fuzzier; don’t obsess over precise counts.
- Attribution gets noisy earlier than product funnels.
- Be transparent: label directional dashboards as directional.
- Use consent signals to change behavior, not to “game” tracking.
- Collect fewer, better events—noise hurts more in cookieless setups.
- Never send personal data in event properties.
- Server-side collection can improve stability and validation.
- If you need long-term identity, use login moments—not guesswork.